Detect and prevent highly complex and sophisticated attacks – effectively and in real time
Use Hornetsecurity ATP to protect your business against individually targetted attacks starting from the first malicious email. Highly innovative forensic analysis engines ensure that the attacks are stopped immeidately. At the same time the solution provides detailed information about the attacks on the company.
Advanced Threat Protection Protects Your Email Traffic From Insidious Cyber Attacks

Protection Against Blended Attacks
Blended attacks use different types of malware at the same time. Viruses, spyware, spam and phishing are combined in one email attack.
This blending of attack methods and penetration of different vulnerabilities makes cyber attacks even more complex and difficult to detect.

The new ATP feature: Malicious Document Decryption
Classic anti-virus programs cannot detect the malware hidden by this encryption. Malicious Document Decryption adds another essential feature to Advanced Threat Protection: encrypted email attachments are decrypted using appropriate text modules. The decrypted document is then subjected to an in-depth virus scan. This keeps your mailbox safe from even this advanced threat.

Increasing Threat from Ransomware
Ransomware is one of the most popular methods of cyber crime in terms of both profitability and scope of (financial) damage to the victims. If the blackmailer’s software infiltrates a company system, all sensitive and confidential files are encrypted and are only released in exchange for a ransom in the form of Bitcoins. Unfortunately, there is no guarantee the files will actually be released after payment has been made.
A Strong Alliance Against All Methods of Attack
The variety of attack vectors means defense mechanisms must be able to cope with a multitude of methods in order to ward off all potential threats. That’s why Hornetsecurity uses freezing, URL scanning, rewriting and sandboxing to keep threats away from your IT infrastructure.
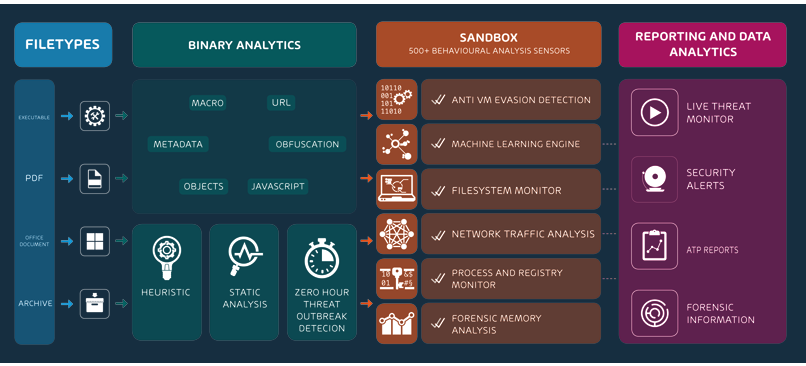
Comprehensive risk analyses with Sandbox Engine: Dangerous types of malware
Dangerous types of malware such as Emotet, Hancinator and Trickbot often hide behind file attachments in emails and therefore remain undetected at first. However, as soon as an infected document is opened, the malware enters a company’s system and can cause millions of dollars of damage. The Sandbox Engine scans email attachments for potential malware by running the file in a virtual, isolated test environment where any potentially harmful effects can be safely identified.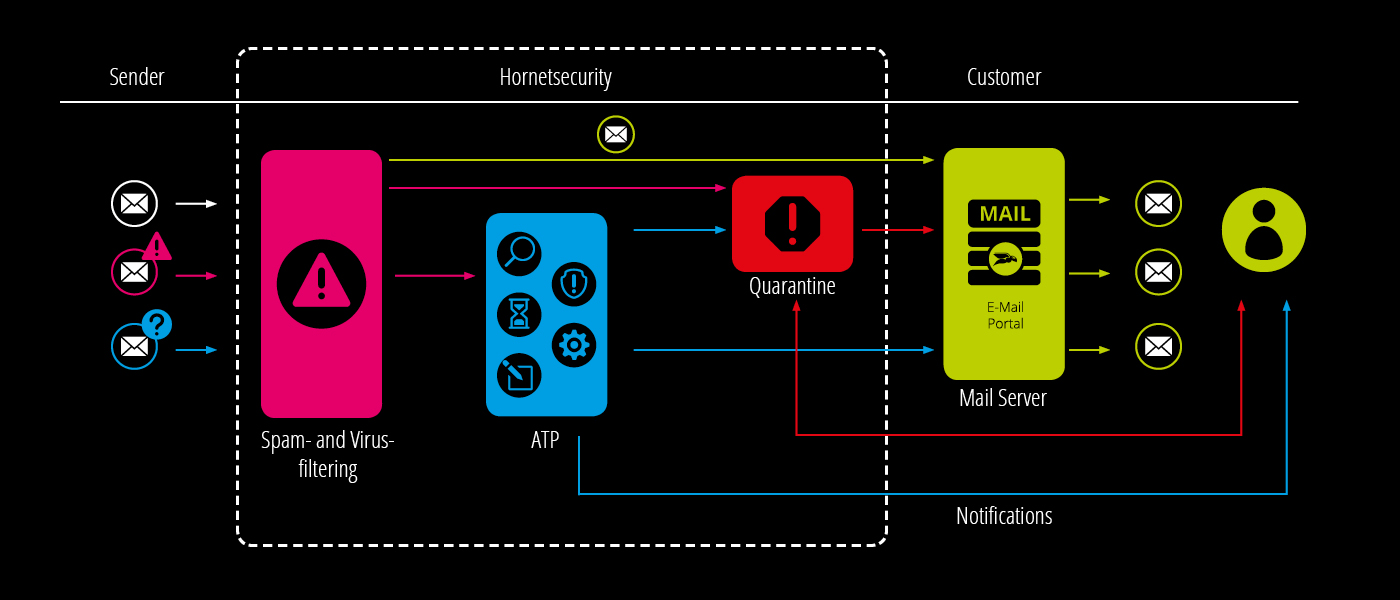
If the document sent turns out to be malware, the emails are quarantined directly, and the company’s IT security team is notified.
Freezing is the safe option
Emails that cannot be classified definitively straight away but are suspicious are held back for a short time by freezing them. The email is re-scanned – as soon as the virus-detection engines get a hit, the email is moved directly into quarantine. Ransomware, blended attacks, and phishing attacks will never get into your email inbox again!
URL Rewriting
Security with every click with URL rewriting secures all Internet access from emails via the Web Filter Engine. When you click on a link in an email, it is replaced by a secure URL. The user is then forwarded to the secured website via the Hornetsecurity web filter. The websites leading from the target page are also secured by URL rewriting.
This means that no malicious code can be downloaded to the computer unnoticed. Downloads from the web are also analyzed via the Sandbox Engine, which immediately aborts the download when malware is detected.
No getting through for harmful links thanks to URL scanning
Documents attached to an email (e.g. PDF, Microsoft Office) often contain further links. However, these cannot be replaced as this would violate the integrity of the document. The URL scanning engine leaves the document in its original form and only checks the target of these links to rule out possible malware damage and prevent phishing attacks.
Real-Time Alerts
Hornetsecurity Real-Time Alerts notify your IT security teams in real-time about acute attacks on your company. This up-to-date information can be used directly by the company for countermeasures so that you can close your security loopholes in the shortest possible time and set up additional protective measures.
Ex-Post Alerts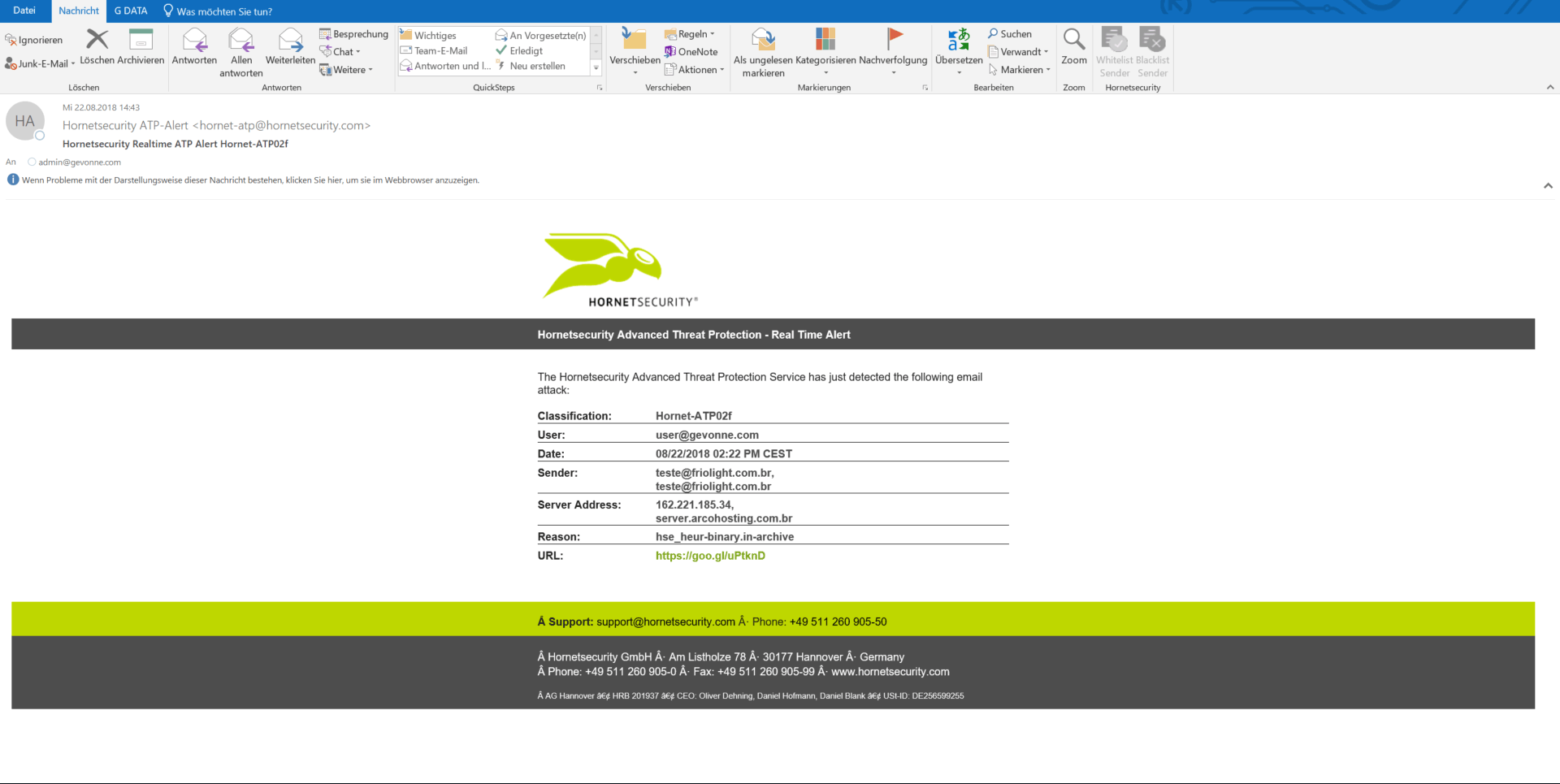
With the ex-post alert, your IT security team receives an automatic notification if an email that has already been delivered is subsequently classified as malicious. You will receive a detailed evaluation of the attack so that you can immediately initiate measures such as checking systems and raising the awareness of your own employees.
If a virus or infected link is detected in ATP analysis tools such as the Sandbox Engine or URL scanning, the system automatically sends an alert. In addition, the administrator is informed about the attempted intrusion into the IT structure. This alert contains detailed information about the type and extent of the attack.
Targeted Fraud Forensics Includes
The Following Intelligent Detection Mechanisms

Protection Against Digital Espionage
Checks the authenticity and integrity of metadata and mail content.

Identity Spoofing Recognition
Detection and blocking of forged sender identities.

Intention Recognition System
Alerting to content patterns that suggest malicious intent.

Spy-Out Detection
Defense against espionage attacks to obtain sensitive information.

False Facts Identification
Identity-independent content analysis to identify messages that attempt to induce the recipient to take action by putting forward fictitious facts.

Targeted Attack Detection
Detection of targeted attacks on individuals who are particularly at risk.
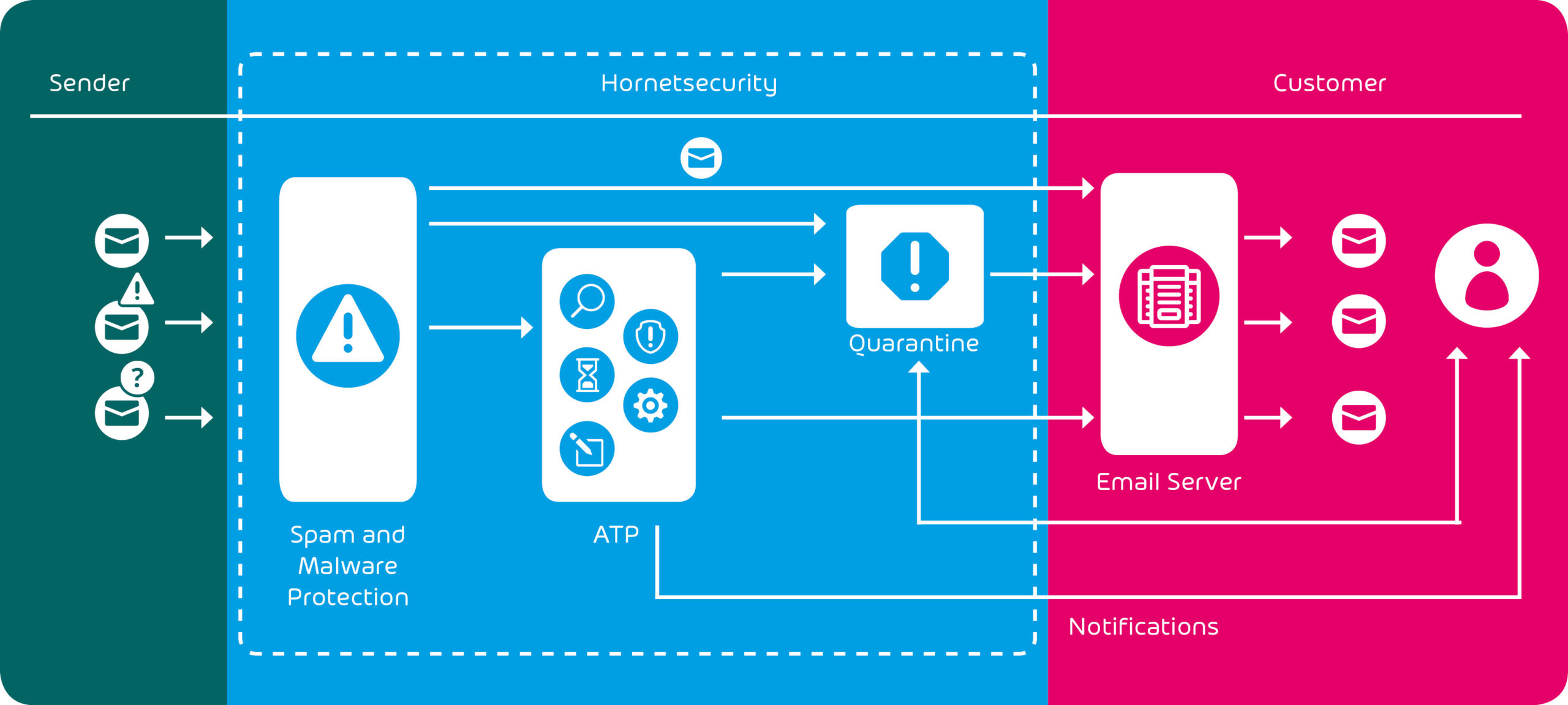
Integration of Hornetsecurity ATP into Email Security Management
Hornetsecurity ATP integrates seamlessly into spam and virus filters. Emails that have passed this first test are subjected to further analysis by Hornetsecurity ATP. Among other things, the service executes attachments and observes their behavior in detail.